Connecting ATCOM+ to Facility Heat Trace Infrastructure: LAN Connection
Network Architecture, System Requirements and Security Overview
Background:
ATCOM+, a cloud-based heat trace monitoring and management application, offers seamless access to critical heat trace systems from any location with internet connectivity. As a cloud-based platform, ATCOM+ ensures users have access to the latest updates and features while maintaining robust security measures to protect sensitive data.
Purpose:
This article aims to provide insights into the network architecture and facility requirements necessary to integrate ATCOM+ with existing heat trace infrastructure. Additionally, it delves into the functional aspects of the ATCOM+ platform and emphasizes its importance in modern facility management.
Overview:
ATCOM+ operates within a cloud-based architecture, offering accessibility and flexibility while maintaining robust security protocols. Here's how data flows within the ATCOM+ ecosystem and the security measures in place to safeguard sensitive information:
-
Heat Trace Equipment:
Connected to a dedicated LAN or VLAN within the facility's network infrastructure, heat trace equipment forms the foundation of the ATCOM+ ecosystem -
ATCOM+ Service Application:
Installed on a Windows machine or virtual machine within the Process Control Network (PCN), the ATCOM+ Service application facilitates communication with heat trace controllers. This service is responsible for Modbus communication to the heat trace equipment, enabling seamless data exchange and real-time monitoring. It initiates only outbound communications to the ATCOM+ cloud application, ensuring that no external entities can access facility hardware directly. -
ATCOM+ Marshal Application:
-
DMZ Layer Deployment: Positioned on the DMZ server layer(s), the ATCOM+ Marshal application serves as a proxy server, orchestrating secure communication between network layers. It enforces access controls to ensure that only authorized traffic passes between the Process Control Network (PCN) and the DMZ layer, maintaining data integrity and security.
-
BLAN Layer Deployment: Installed within the BLAN layer, the ATCOM+ Marshal application extends its functionality to secure communication between the DMZ layer and internet-connected layers. By regulating traffic flow and implementing stringent security measures, it safeguards against unauthorized access and potential threats, enhancing overall network security posture.
-
-
ATCOM+ Cloud Servers:
ATCOM+ cloud servers serve as the central hub for data processing and analysis. All communication between the ATCOM+ Service application and cloud servers is encrypted using Transport Layer Security (TLS), ensuring data integrity and confidentiality.
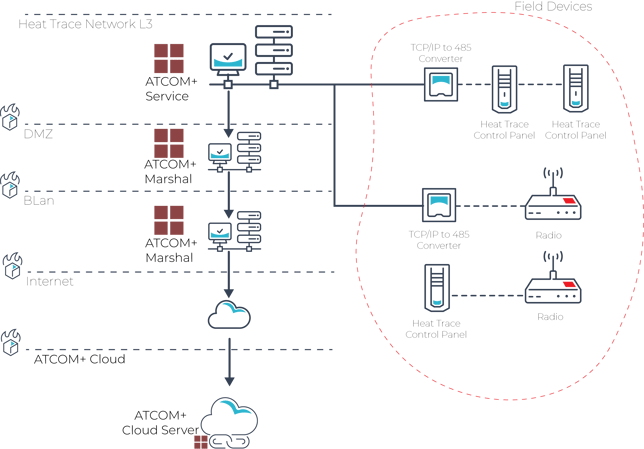
In this facility, a 3-layer network approach was chosen for security and efficiency. Field devices connect to the Process Control Network (PCN), isolated from the internet. The ATCOM+ Service, responsible for Modbus communication with heat trace equipment, runs on a Windows machine within this network. The DMZ layer acts as a separation layer without internet access. At the highest layer, the BLan layer has internet access. To ensure secure communication, ATCOM+ Marshal, a proxy server, manages traffic between layers. Two ATCOM+ Marshal VMs are deployed – one in the DMZ layer and another in the BLan layer. Additionally, the ATCOM+ Service initiates all communication to the cloud servers; no communication can be initiated by the cloud service.
Multiple ATCOM+ Service applications may be deployed depending on the size of the heat trace infrastructure and to optimize Modbus communication.
Security:
ATCOM+ prioritizes security at every level of its architecture. Here's how:
-
End-to-End Encryption: All communications within the ATCOM+ ecosystem, including those between the ATCOM+ Service application and cloud servers, are encrypted using TLS, with support up to version 1.3. This ensures that data remains confidential and protected from unauthorized access.
- Outbound Communication: The ATCOM+ Service is never passively listening for requests. Instead, it operates as a client of the ATCOM+ cloud, which means all requests are initiated internally from the ATCOM+ Service itself. The f
irewall will reject all ingress traffic except for the responses to requests initiated internally. This outbound communication model minimizes security vulnerabilities and enhances control over data flow. - Access Controls:
- Two-Factor Authentication (2FA): 2FA can be enforced to add an additional layer of security for user access.
- Strong Password Security: Passwords are required to meet strong security standards and must be changed periodically as per company policies.
- Single Sign-On (SSO): ATCOM+ supports Microsoft Azure SSO, allowing seamless and secure user authentication.
- Granular Access Control Lists (ACLs): Granular ACLs allow administrators to assign different levels of access to users based on their roles, ensuring that only authorized personnel have access to specific process equipment.
- Firewall and Network Security:
- Firewall Settings: The firewall can be configured to reject all ingress traffic except responses to requests initiated internally, providing an additional layer of protection.
- No Open Ports: ATCOM+ does not have any active ports opened and listening for incoming requests, reducing potential entry points for unauthorized access.
- Multi-Layer Network Support: ATCOM+ supports multi-layer networks through the use of the ATCOM+ Marshal, ensuring secure and efficient communication between network layers.
These robust security measures ensure that ATCOM+ provides a secure environment for managing and monitoring your heat trace systems, protecting both data and infrastructure from potential threats.
Requirements:
To ensure a seamless integration process, facilities must meet specific hardware and software requirements:
-
Minimum OS: Windows 11 Pro (or equivalent), installed within the PCN.
- RAM: 16GB
- Processor: 12th Gen Intel Core i7-13700T (or equivalent)
-
ATCOM+ Marshal Installations (2x, can be VM)
- RAM: 4GB
- CPU: 1 Core
Custom ATCOM+ Integration
While ATCOM+ is designed as a comprehensive cloud application, we recognize that different facilities have unique needs and requirements. To cater to these varying needs, we offer a customized installation option:
ATCOM+ Cloud - Read Only / ATCOM+ On-Site Server - Read-Write:
In this setup, ATCOM+ users accessing the system via the cloud have read-only access to heat trace information and cannot make any programming modifications. This is accomplished by configuring the client’s network to block all incoming write requests from the cloud.
However, read-write access is enabled when users access ATCOM+ from an on-site server within their network. In this configuration, users can make necessary programming modifications directly from their local network. This setup involves establishing a custom API connection to ATCOM+ with custom TLS certificates initiated from the client servers.
This hybrid approach provides flexibility, ensuring that ATCOM+ can be integrated seamlessly into various operational environments. Whether your facility prioritizes remote monitoring or requires direct local control, ATCOM+ offers the adaptability to meet your specific needs.
For more information regarding this installation please contact support@ehtgroup.com
By adhering to these requirements and understanding the security measures in place, IT professionals can confidently integrate ATCOM+ into their facility's network infrastructure, unlocking advanced heat trace monitoring and management capabilities while ensuring data security and integrity.
